Tangem vs Ledger: Which Hardware Wallet Offers Better Security in 2026?
Tangem users and anyone researching self-custody options deserve accurate information to make informed decisions

- AI summary
- Tangem’s card-based architecture
- Ledger’s architecture
- Trusted display or false sense of security?
- Tangem’s model
- Updatable vs. immutable firmware
- The seed phrase: crypto’s biggest attack vector
- Vault vs. custom operating system
- EAL certification
- Open source and transparency
- Security evaluation: Independent vs. Internal
- PIN on device vs. on phone
- Tangem Mobile Wallet
- Security track record
- Ecosystem and asset support
- Pricing and value
- Comparison tables
- Summary
AI summary
The best hardware wallet keeps your crypto safe while being simple enough for you to actually use. We explain why Tangem is the right choice.
- Ledgers force every user to generate, write down, and physically secure a 24-word seed phrase; the single largest attack vector in consumer crypto. Tangem’s seedless-by-default model eliminates this risk entirely. No phrase to write down means no phrase to photograph, phish, or steal.
- Ledger’s firmware updates are a vulnerability because every update mechanism is a code-injection pathway into the device. Tangem’s immutable firmware eliminates this entire attack category: no update mechanism means no remote exploit vector.
- Ledger’s architecture, USB ports, Bluetooth, rechargeable batteries, custom OS, screen drivers, and firmware update pipelines introduce attack surfaces that Tangem’s minimalist design simply does not have.
- Blind Signing refers to approving a transaction on a hardware wallet without full visibility into its details. Tangem has solved the blind signing problem in a way that Ledger’s Signers have failed to do.
Today, we’ll compare Tangem cards with Ledger signers to examine what each actually delivers in practice. The differences begin with the fundamentals: what each device is designed to protect you from, and how that protection holds up in the real world.
Tangem’s card-based architecture
Tangem is a credit-card-sized NFC wallet with an EAL6+ certified Secure Element. It has no screen, no buttons, no battery, no USB port, and no firmware update mechanism. You tap it against your phone to sign transactions. It’s IP69K waterproof and dustproof.
The Tangem Wallet is not minimalist for aesthetic reasons. Every component removed is an attack surface eliminated:
- No screen means no screen driver that could be exploited, no display buffer that could be manipulated, and no additional chip-to-screen communication channel to intercept.
- No USB port means no physical data exfiltration channel, no BadUSB-style attacks, and no risk of plugging into a compromised computer.
- No battery means no degradation over time, no thermal events, and a lifespan measured in decades rather than charge cycles.
- No firmware update mechanism means no over-the-air attack vector, no supply chain interception during updates, and no possibility of a malicious update being pushed to your device.
Ledger’s architecture
Ledger’s signers are pocket-sized electronic devices with Secure Element chips, screens (OLED or E-Ink touchscreens), buttons, USB-C ports, Bluetooth connectivity (Nano X), and rechargeable batteries.
They run a custom operating system within the Secure Element and display transaction details on the device’s screen. This is a legitimate security concept in principle, but it introduces trade-offs that are rarely discussed.
Trusted display or false sense of security?
Ledger’s built-in screen is an attack surface.
The communication channel between the Secure Element and the screen driver is an additional interface that must be secured. The Ledger Donjon, the company’s research arm, exists largely because the hardware around Ledger’s Secure Element, including its display pipeline, requires continuous testing and patching.
Tangem’s model
The central argument in favor of screen-based hardware wallets is that your smartphone could be compromised by malware, so you need an independent display to verify transactions.
Modern smartphones include hardware-backed secure environments (Apple’s Secure Enclave and Google’s TEE), biometric authentication, application sandboxing, and verified boot chains. Therefore, the phone hacking argument hasn’t kept pace with advances in mobile security.
Your smartphone already handles your banking, brokerage accounts, government ID verification, and two-factor authentication for your most sensitive accounts.
Regarding mobile security, we have already discussed in detail why the Tangem Wallet doesn't need a screen.
Tangem’s approach is clear.
- You initiate and verify all the transaction details on your smartphone,
- Then tap the card or ring to sign it.
- The card receives the transaction hash via NFC, signs it within the Secure Element, and returns the signature.
At no point does the wallet device need to display anything, because signing occurs only after you’ve confirmed the transaction parameters on your smartphone.
This is not “blind signing,” as Ledger calls it. According to Blockaid, blind signing happens when hardware wallets show limited or no transaction information on the signing interface. You can clearly see the full transaction details in the Tangem app before you tap your card.
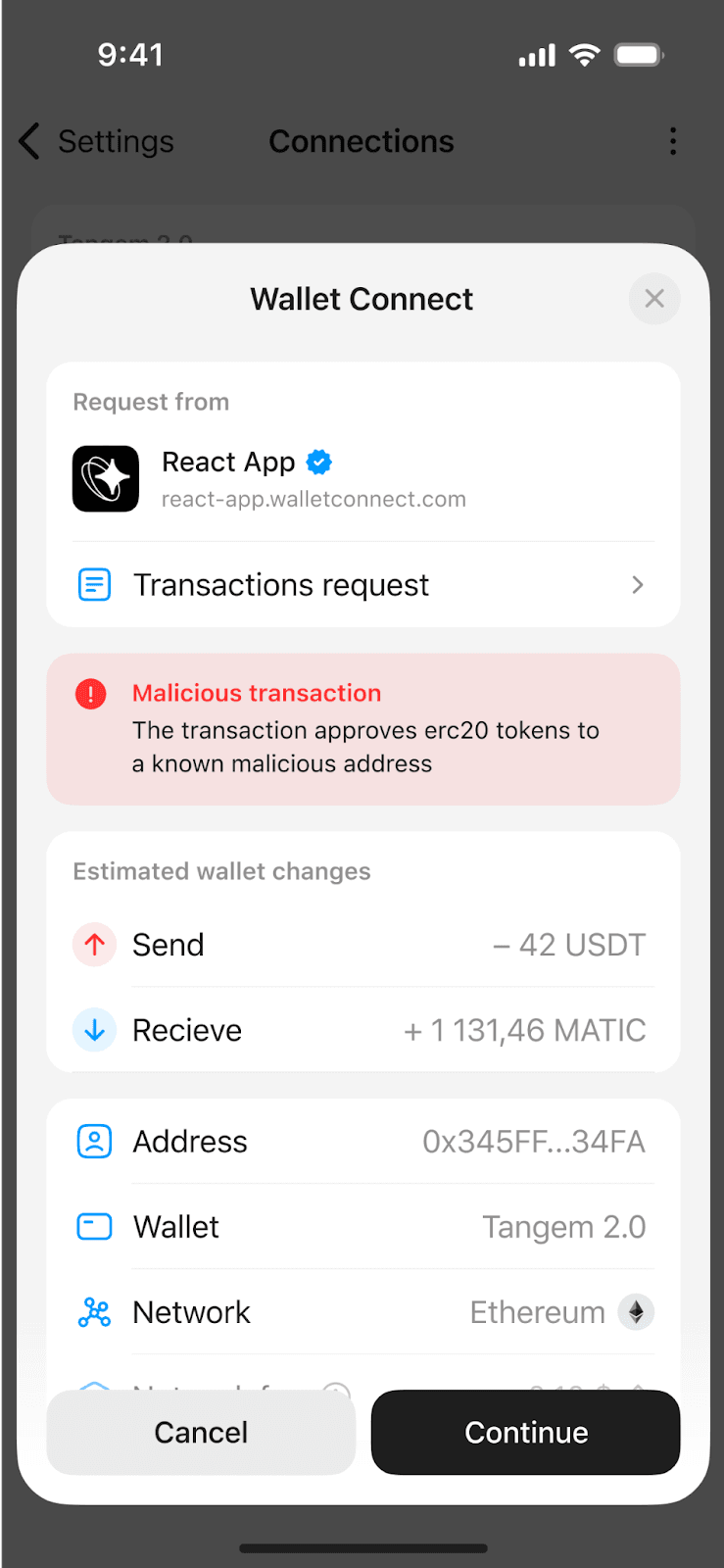
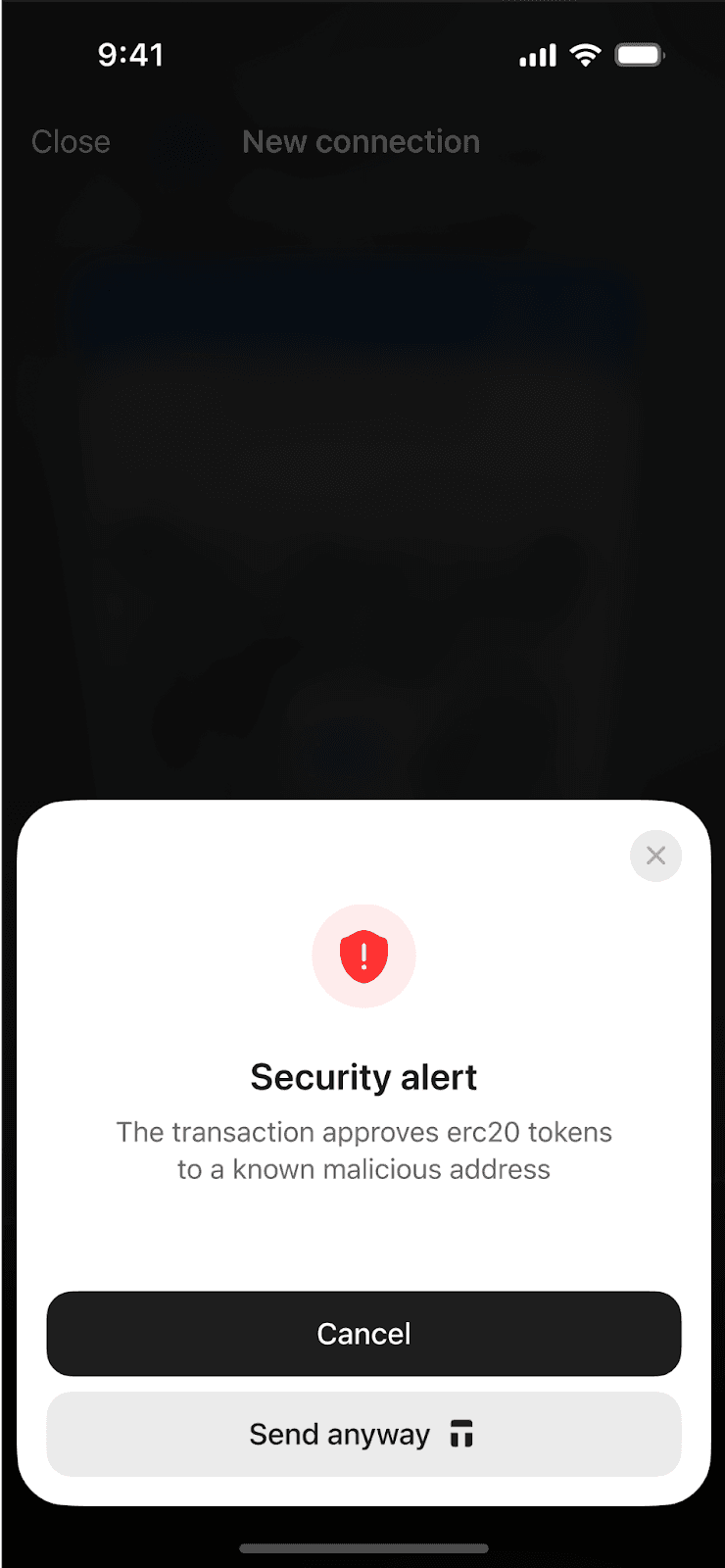

The blind part would be if you never saw the details at all, which is exactly what happens when Ledger users encounter smart contract interactions that haven’t been integrated with Clear Signing, and the device displays only raw hexadecimal data.
Clear Signing has a coverage gap
Ledger’s Clear Signing, based on EIP-7730, was designed to parse smart contract calls into human-readable transaction details displayed on the device’s screen.
Clear Signing works only within Ledger’s own wallet app for supported protocols. But when users connect their Ledger to third-party wallets like MetaMask, Phantom, or Rabby, Clear Signing depends entirely on the dApp or wallet sending parsed transaction metadata to the Ledger.
Ledger acknowledged this: “For complex smart contract interactions, you may still encounter blind signing prompts if the dApp doesn’t provide full transaction details.”
Where Clear Signing has failed
Blind signing still happens for a significant portion of verification activity. For example, Ledger’s Clear Signing or secure screen didn’t stop Bybit from getting hacked after signing a malicious transaction with a Ledger signer, leading to a loss of $1.5 billion (the largest in recent times).

In practice, the screen might work when users need it least (simple transfers) and revert to blind signing when they need it most (complex smart contract interactions). That makes it fair to assume that Ledger’s marketing has been aggressively focusing on Clear Signing as a major security issue to push sales for their newer, more expensive models with e-ink screens.
With Tangem, there’s no false sense of security from a screen that sometimes shows you details and sometimes doesn’t.
Updatable vs. immutable firmware
An updatable firmware is a vulnerability
Ledger positions firmware updates as a clear advantage, enabling the patching of vulnerabilities, adding new features, and supporting new types of blockchains. But every firmware update mechanism is a code injection pathway into the device. If the update mechanism exists, it can potentially be exploited. The launch of Ledger Recover, a paid subscription service where your private keys are stored with custodians, proved this.
Consider what a firmware update requires: the device must accept external code, validate it, and overwrite its existing operating instructions.
This creates an attack surface that includes:
- supply-chain interception (compromising the update before it reaches the device),
- man-in-the-middle attacks during the update process,
- exploitation of the validation mechanism itself,
- and social engineering that tricks users into installing malicious firmware.
Ledger’s security model requires continuous vigilance from the Donjon team because the update surface exists and must be constantly defended.
Immutable firmware is security via elimination
Tangem’s firmware cannot be updated. From an engineering perspective, it’s a deliberate choice that eliminates an entire category of attacks.
If no code can be written to the device after it leaves the factory, there is literally no mechanism for a remote attacker to alter its behavior.
It is true that if a vulnerability is discovered in the card’s cryptographic implementation, the fix requires new hardware. But this trade-off must be weighed against the risk profile of each approach.
Ledger’s approach: Continuous exposure to firmware-level attack vectors, mitigated by continuous defense. If the defense fails once, every device is potentially compromised.
Tangem’s approach: Zero exposure to firmware-level attack vectors post-manufacture. The only vulnerability is in the original factory firmware, which has been independently audited by two of the world’s leading embedded security firms, Riscure and Kudelski.
The seed phrase: crypto’s biggest attack vector
The 12-24 word seed phrase is the foundation of the BIP-39 standard, and Ledger correctly notes that it provides universal recovery across any compatible wallet. This is a genuine advantage for interoperability.
However, the seed phrase is, by an overwhelming margin, the single largest source of crypto theft in the consumer market.
Phishing attacks that trick users into revealing their seed phrase, physical theft of written seed phrases, photographs of recovery cards, and clipboard malware collectively account for far more consumer crypto losses than all phone hacking or supply chain attacks combined.
Tangem’s seedless model
Tangem’s default setup generates keys on the card’s Secure Element and backs them up across 2–3 physical cards with identical key material. No seed phrase is generated, written, or stored anywhere. The keys exist only inside the Secure Element chips of the physical cards you hold. This eliminates the entire category of seed phrase attacks.
For users who want a seed phrase backup (for example, to maintain compatibility with other wallets), Tangem offers this option. But we strongly believe that the default seedless configuration is the most secure consumer key management model available today.
Ledger’s other recovery options
As mentioned above, Ledger has been marketing additional paid options, such as the Recovery Key (a PIN-protected backup card) and Ledger Recover (an encrypted cloud backup service). Here’s how our approach compares to their cloud backup service: Ledger Recover vs Tangem’s Seedless Wallet: What’s the Safest Way to Store Private Keys
Vault vs. custom operating system
Ledger runs a custom operating system within its Secure Element, enabling app isolation, on-device screen management, and per-blockchain applications. This creates a rich execution environment inside the secure chip. Every line of code running on the Secure Element must be secured, tested, and protected against exploitation.
The custom OS, the app sandbox, the screen driver, the Bluetooth stack (Nano X), the USB interface, and the firmware update mechanism all represent code paths that could contain vulnerabilities.
Tangem’s Secure Element chip operates as a cryptographic vault: it generates keys, stores them, receives transaction hashes via NFC, signs them, and returns signatures. The code running on the chip is minimal and purpose-built. Less code means fewer potential vulnerabilities and a system that is easier to audit comprehensively.
EAL certification
Both Tangem and most current Ledger models use EAL6+ certified Secure Element chips. The Ledger Nano X uses an EAL5+ chip. EAL certification evaluates the chip’s resistance to physical attacks, not the security of the software running on it.
On this particular metric, the current Ledger models are quite similar, with Tangem having a slight edge over the Nano X. However, as Ledger rightly points out, certification by itself doesn’t tell the whole story about security.
Open source and transparency
The open source question is nuanced for both wallets. Tangem’s mobile app is open source; its firmware is closed source but audited. And you can verify your card/ring has the audited firmware.
Ledger’s custom OS is closed source, and Ledger Live is partially open source, but not fully reproducible or fully auditable end-to-end. Neither company is fully open source across the entire stack. However, a bug in Ledger’s firmware would be invisible until Ledger chose to disclose it.
Security evaluation: Independent vs. Internal
The Ledger DonJon is an internal security team. No matter how talented, they operate within institutional dynamics. They share office space, company culture, and incentive structures with the development team. They’re subject to the same blind spots, assumptions, and organizational pressures.
Tangem’s firmware went through independent third-party audits by Kudelski Security and Riscure. The auditors have no institutional incentive to minimize or explain away findings.
Bug bounty program
Tangem runs an active bug bounty program that complements its external audits by keeping security testing continuous rather than periodic. The program invites security researchers and ethical hackers to identify vulnerabilities in Tangem's mobile app code, API integrations, and other systems, with rewards based on severity and impact.
PIN on device vs. on phone
Ledger requires a 4–8 digit PIN entered on the device’s screen. After three wrong attempts, the device wipes. Tangem uses an access code entered on your phone, with biometric authentication (Face ID or fingerprint) as an additional layer of security.
Ledger’s argument that PIN entry on the device is more secure than phone-based authentication ignores the advances in mobile security. Modern smartphone authentication combines hardware-backed secure enclaves, biometric sensors with liveness detection, and OS-level encryption.
A 4-digit PIN entered on a small screen in public is arguably more vulnerable to shoulder surfing than a biometric authentication on a phone. And biometric authentication cannot be phished or coerced in the same way a PIN can.
Tangem Mobile Wallet
The Mobile Wallet exists to serve a real user need (onboarding users to self-custody), targeted towards those who are not ready to commit to hardware. The Tangem app differentiates between hardware-backed and mobile wallets with distinct labeling and visual indicators. The mobile wallet’s code is also open-source on GitHub and has been independently audited by Cure53.
Ledger’s ecosystem requires users to navigate between the Ledger Wallet app, MetaMask, Phantom, Rabby, and various other hot wallet integrations, each with its own security model.
Security track record
Both Tangem and Ledger can claim that no private keys have been compromised through their hardware. This is the bare minimum for a hardware wallet, and both clear it.
Where the track records diverge is in the broader impact of security incidents on actual users.
2020: Ledger customer database breach
A customer database breach exposed the personal information of over 270,000 customers, including names, physical addresses, email addresses, and phone numbers, and compromised a wider marketing database of approximately 1 million email addresses. This led to sustained phishing campaigns, physical threats, and SIM-swap attacks targeting Ledger users. The leaked database remains publicly available on various forums.
2023: Ledger Connect Kit supply chain attack
In December 2023, attackers compromised Ledger’s Connect Kit, an open-source JavaScript library used by dozens of decentralized applications to interface with Ledger devices. The attacker phished a former Ledger employee whose access to the npm package manager had not been properly revoked during offboarding, then published malicious versions of the library that redirected funds to attacker-controlled wallets.
The malicious code was live for approximately five hours and resulted in the theft of over $600,000 in user funds across multiple DeFi platforms, including Revoke.cash, SushiSwap, and others. The attack affected not just Ledger users but anyone interacting with DApps that used Ledger’s library.
2026: Global-e Vendor data breach
A Global-e vendor breach exposed additional customer data, the full extent of which was not immediately disclosed.
Ledger’s incidents put users’ physical safety at risk and created lasting exposure that persists to this day.
Ecosystem and asset support
Tangem's 85+ blockchain coverage already exceeds Ledger Live's native support, and Ledger's broader numbers (5,500+ assets) rely heavily on third-party wallet integrations, not native Ledger Live support.
Tangem supports all major blockchains, Bitcoin, Ethereum, Solana, and the full EVM ecosystem, along with 16000+ tokens through its universal signing architecture. For the vast majority of crypto users, Tangem covers all the assets they actually hold.
Tangem has native swap functionality and staking capabilities through in-app integrations, while maintaining the security benefits of the hardware wallet.
Pricing and value
Tangem’s 3-card set costs $69.90 and includes built-in redundancy across three physical backup cards. Ledger’s touchscreen devices range from $149 to $399, with the Ledger Stax at $399.
The price difference means Tangem delivers protection at a fraction of the cost. For a user securing their first hardware wallet, the lower financial barrier means less hesitation and faster adoption of self-custody.
Comparison tables
Form Factor & Design
Feature | Tangem | Ledger |
|---|---|---|
Device Type | NFC card (credit card size) | Electronic device with screen |
Screen | None required | Touchscreen (OLED/E-Ink) |
Battery | None required (decades of lifespan) | Rechargeable (limited lifespan) |
Waterproof | Yes (IP69K) | No (careful usage needed) |
| Dustproof | Yes (IP69K) | No (careful usage needed) |
| NFC | Yes | No |
USB Port | None (eliminates data channel) | USB-C (additional attack surface) |
Bluetooth | None | Yes on Nano X (additional attack surface) |
Portability | Fits in a wallet like a credit card | Pocket-sized device |
Security Architecture
Feature | Tangem | Ledger |
|---|---|---|
Secure Element Cert. | EAL6+ | EAL6+ (most) / EAL5+ (Nano X) |
Firmware | Immutable (no update vector) | Updatable (continuous patch surface) |
Attack Surface | Minimal (NFC + SE only) | Larger (USB, BT, screen, OS, updater) |
Remote Exploit Risk | Zero (no update mechanism) | Non-zero (update mechanism exists) |
Key Management & Recovery
Feature | Tangem | Ledger |
|---|---|---|
Default Setup | Seedless (keys on cards only) | Seed phrase required (24 words) |
Seed Phrase and Passphrase | Optional (user’s choice) | Mandatory |
Backup Method | 2–3 physical cards | seed phrase + optional add-ons |
Seed Phrase Theft Risk | Eliminated by default | Primary attack vector |
Physical Coercion Risk | Seedless setup option means there’s no seed to surrender | Seed phrase can be coerced |
Universal Recovery | Optional (if seed enabled) | Yes (BIP-39 standard) |
Vendor Lock-in Risk | Low (Seed phrase supported) | Low (BIP-39 standard) |
Authentication
Feature | Tangem | Ledger |
|---|---|---|
Method | Access code + phone biometrics | 4–8 digit PIN on device |
Biometric Support | Face ID / Fingerprint | None |
Failed Attempts | Rate-limited delay | 3 attempts → wipe everything |
Shoulder-Surfing Risk | Low (biometric) | Higher (PIN on small screen) |
Security Track Record
Feature | Tangem | Ledger |
|---|---|---|
Keys Compromised | Never | Never |
Customer Data Breaches | None | 2020 breach (270K+ users exposed) |
Physical Safety Impact | None | Phishing, threats, SIM-swaps |
Software Bugs | 2024 app log bug (patched) | Various (patched via updates) |
Independent Audits | Kudelski (2018), Riscure (2023), Cure53 (2026) | Internal Donjon team |
Ecosystem
Feature | Tangem | Ledger |
|---|---|---|
Supported Assets | All major chains + tokens (over 15000) | ~5,000+ |
Native Swaps | Yes | Yes |
Native Staking | Yes | Yes |
Web3 Integrations | WalletConnect support | MetaMask, Phantom, Rabby |
FIDO2 Passkey | No | Yes |
Mobile Wallet Option | Yes (clearly labeled) | No |
Pricing
Feature | Tangem | Ledger |
|---|---|---|
Entry Price | $54.90 (2 cards) | $149 (Nano Gen5) |
Full Backup Set | $69.90 (3 cards) | $149–$399 + Recovery Key |
Included Backup | Multi-card redundancy | Paper recovery sheet |
Summary
Unlike Ledger Signers, Tangem Wallets are built on principles established in critical infrastructure: minimize the attack surface, eliminate unnecessary complexity, remove human-error vectors, and make the secure path the easiest path.
Tangem's design eliminates attack surfaces by design. Ledger Signers and its ecosystem introduce a proportionally larger attack surface.
Tangem's immutable firmware eliminates the risk of remote exploits after manufacturing, giving you peace of mind. In contrast, Ledger's updatable firmware can pose ongoing vulnerabilities to code injection, as we've seen with the Ledger Recover launch.
Tangem is seedless by default, allowing users to avoid the #1 cause of consumer crypto theft outright. Ledger mandates a 24-word seed phrase, which remains permanently vulnerable to phishing, theft, and physical coercion.
Regarding blind signing, Tangem shows full transaction details in-app before you sign with the card. Ledger's “Clear Signing” has real coverage gaps with third-party wallets and complex smart contracts, as evidenced by the $1.5B Bybit hack.
Tangem also supports Face ID and fingerprint biometrics with rate-limited lockout. Ledger relies on a PIN on a small screen, with just 3 failed attempts before a full device wipe.
The Tangem firmware has been independently audited by Kudelski, Riscure. Cure53 audited the Mobile Wallet, and our public bug bounty program ensures security checks are a continuous process. Ledger relies primarily on its internal Donjon team. They might be competent, but they are not independent.
Ledger has repeatedly suffered customer data breaches in exposing users to targeted phishing and physical threats. Tangem has no such incident.
A complete Tangem 3-card backup set runs $69.90. A comparable Ledger setup (device + Recovery Key) starts at $149 and can cost up to $399+.
More security, less complexity, and at a fraction of the price. The choice really isn't close.