Ledger Recover vs Tangem Seedless: Best Way to Protect Private Keys?
Ledger splits your seed phrase into shards held by third parties. Tangem eliminates seed phrases entirely. Which is safer?

AI summary
Ledger Recover adds trust, attack surface, and government leverage. Tangem removes all three.
TL; DR
Ledger Recover breaks the original hardware-wallet promise: keys never leave the device.
It introduces remote seed extraction, cloud custody, identity verification, and legal exposure across multiple jurisdictions.
Even if a user never opts in, the capability for seed extraction exists on every updated Ledger device. If software can extract keys once, it can do so again—by bug, breach, coercion, or court order.
Tangem takes the opposite approach. No seed phrase is ever created. Keys never leave the Secure Element. Backup is purely physical via multiple cards held by the user—no servers, no custodians, no KYC, no subscriptions.
In May 2023, Ledger announced Ledger Recover, an opt-in subscription service ($9.99/month) that allows users to create a cloud-based backup of their seed phrase. The announcement triggered one of the most significant backlash in hardware wallet history, with security researchers publicly questioning the service’s implications.
Ledger has since launched the service and continues to market it. Understanding what Ledger Recover actually does, and what it means for the security model, is essential for any user evaluating hardware wallet options.
What is Ledger Recover, and how does it work?
When a user subscribes to Ledger Recover, the device’s firmware encrypts a version of the seed phrase’s entropy, splits it into three encrypted fragments (shards) using Shamir Secret Sharing, and sends each shard to a different third-party custodian: Ledger, Coincover, and EscrowTech.
To use Recover, the user must pass an identity verification process using a government-issued ID and facial recognition. Two of the three custodians then send their shards back to the user’s Ledger device, where they are reassembled to reconstruct the seed phrase.
The service costs $9.99 monthly. If the user ceases payments, access to the backup will eventually be revoked. To regain access after the subscription is suspended, the user must pay a 50 EUR administration fee along with any remaining balance.
The seed phrase extraction problem
The core controversy is about what the service’s existence reveals about the device’s capabilities.
Before Ledger Recover was announced, users operated under the assumption that the Secure Element was a one-way vault: keys go in, signatures come out, nothing else leaves. Ledger’s own marketing reinforced this understanding.
A Ledger post on X had previously mentioned that firmware updates cannot extract the seed from the Secure Element.
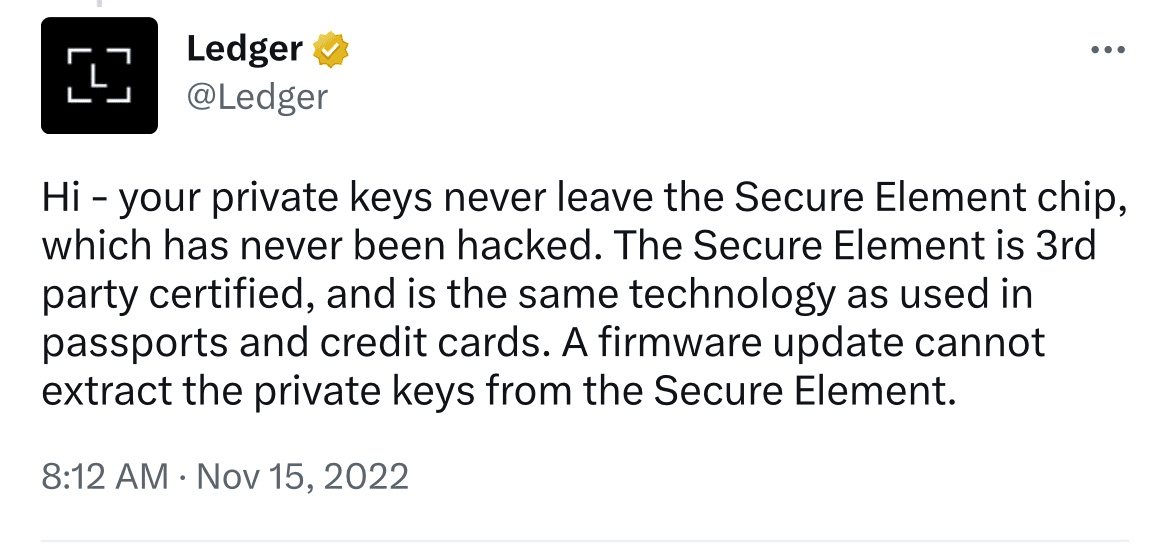
Ledger Recover proved this was incomplete. The firmware does have the capability to extract seed phrase data from the Secure Element and transmit it to external parties.
Ledger’s former CEO and co-founder, Éric Larchevêque, later acknowledged that the previous statement was missing the caveat “as long as you are trusting Ledger.”
The service launch revealed that Ledger firmware has the technical ability to extract and transmit seed phrase material. This capability exists on every device running the updated firmware, regardless of whether the user subscribes to the service.
Tangem’s default setup never generates a seed phrase. Private keys exist only inside the Secure Element chips of your physical cards. There is no firmware capability for extracting keys from the card. This isn’t a policy choice that could be reversed; Tangem cannot update firmware on existing devices.
The government subpoena admission
In a podcast interview following the announcement, Ledger CEO Pascal Gauthier was asked directly whether governments could access users’ seed phrases through the Ledger Recover service.
His response was unambiguous: the “only concern” is if the company is subpoenaed by a government, in which case the three custodians could be compelled to hand over the shards.
- Ledger is based in France (EU), headquartered in Paris.
- Coincover is registered in the United Kingdom, regulated by the FCA.
- EscrowTech is headquartered in Utah, US
The encrypted seed phrase shards are now subject to three independent legal systems, each with its own surveillance and compulsion powers, and a subpoena in any one of them can compromise a shard.
France operates under EU data protection (GDPR) but also has broad national security powers. The UK, post-Brexit, operates under its own data regime and the Investigatory Powers Act, which grants extensive government access to data held by UK companies.
The US has the broadest toolkit: FBI National Security Letters, FISA court orders, and standard federal subpoenas, all of which can compel Utah-based EscrowTech to hand over materials, often with gag orders preventing disclosure to the user.
The critical problem with Shamir Secret Sharing in a 2-of-3 scheme is that compromising any two of the three custodians reconstructs the full seed.
So, a coordinated request between just two of these jurisdictions, say a US-UK mutual legal assistance treaty (MLAT) request, or a Five Eyes intelligence-sharing arrangement (the UK and US are both members), could theoretically reconstruct a user's keys without the user ever knowing.
Even without coordination, the sheer surface area could be a problem. Three different governments, three different legal standards for compulsion, and three different breach notification regimes.
“Criminals don’t use cryptos much.”
Gauthier downplayed this risk, arguing that governments issue such subpoenas only in cases involving serious criminal activity, while, in his opinion, “criminals don’t use cryptos much”. He therefore acknowledged that a legal mechanism exists for third parties to access users' seed phrases who opt into Ledger Recover.
When the podcast host pointed out that the IRS had previously subpoenaed user information from Coinbase (affecting 13,000 users), Gauthier argued that Ledger is not a banking institution and would not face the same legal constraints.
Whether this legal distinction would actually hold up under pressure from determined government agencies remains untested.
The KYC issue
Ledger Recover requires identity verification using a government-issued ID and facial recognition. Ledger insists this is identity verification, not KYC, but the practical distinction is narrow. Effectively, users are linking their real-world identity to their hardware wallet’s seed phrase backup.
This creates a database that didn’t previously exist: a mapping of verified identities to encrypted seed phrase fragments. Even if the encryption is strong, the existence of this database is itself a target.
The closed-source trust problem
Ledger’s firmware is closed source. Users cannot independently verify what code is running on their device. This means there is no way for the community to confirm whether the seed phrase extraction capability is limited to the Recover service or cannot be triggered without user consent.
Ledger has committed to open-sourcing more of its code over time, but the core firmware remains proprietary. There are no third-party audits either.
The result is that users must trust Ledger’s assurances about what the firmware does and doesn’t do, contradicting the ethos of hardware wallets.
Paying for your own security
Ledger Recover costs $9.99 per month to maintain access to a backup of the hardware wallet's seed phrase. If a user stops paying, they lose access to the backup.
Over five years, that’s approximately $600 in subscription fees, on top of the $149–$399 hardware cost, for a backup of information that the device itself generated.
This is a recurring revenue model built on top of a security architecture that creates the problem (mandatory seed phrase) and then sells users the solution (cloud backup of that phrase).
Tangem’s backup model is physical (2–3 cards with the same private keys). When you set up a wallet, you can link two or three cards that securely generate and store the same private keys.
Each card acts as an independent access point to the same wallet. As long as you keep at least one card safe, you retain full control over your assets. There is no seed phrase to write down, no cloud upload, and no remote recovery mechanism.
A pattern of security incidents
Evaluating whether to trust a company with additional capabilities, such as seed phrase extraction and cloud storage, requires examining its security track record. Ledger’s record reveals a pattern:
2020: customer database breach
In 2020, Ledger suffered a data breach that exposed the personal information of over 270,000 customers, including names, physical home addresses, email addresses, and phone numbers. A wider marketing database of approximately one million email addresses was also compromised.
The leaked database was published on hacking forums and remains publicly available, and still haunts victims to this day. The consequences are severe and personal:
- targeted phishing campaigns impersonating Ledger
- physical threats and extortion attempts directed at users whose home addresses were exposed,
- and SIM-swap attacks using the leaked phone numbers.
No private keys were compromised, but the incident demonstrated that Ledger’s operational security for customer data was not enough.
2023: Connect Kit supply chain attack
In December 2023, attackers compromised Ledger’s Connect Kit, an open-source JavaScript library used by dozens of decentralized applications to interface with Ledger devices.
The attacker phished a former Ledger employee whose access to the npm package manager had not been properly revoked during offboarding, then published malicious versions of the library that redirected funds to attacker-controlled wallets.
The malicious code was live for approximately five hours and resulted in the theft of over $600,000 in user funds across multiple DeFi platforms, including Revoke.cash, SushiSwap, and others. The attack affected not just Ledger users but anyone interacting with DApps that used Ledger’s library.
The root cause was an elementary operational failure: a former employee’s access credentials to a critical deployment channel were not revoked. Ledger’s own post-mortem acknowledged that their offboarding procedures failed to cover npm access.
2026: Global-e Vendor data breach
In January 2026, Ledger confirmed that customer personal data was exposed via a breach at its third-party e-commerce partner, Global-e, which handles checkout and order processing for purchases on Ledger.com. The exposed information included names, contact details, shipping addresses, and order data, though wallets and private keys remained secure.
How Tangem avoids these risks
Tangem’s security architecture was designed from the ground up to minimize trust requirements and eliminate the attack surfaces that have repeatedly caused problems for Ledger.
With Tangem, recovery does not depend on remote servers or coordinated shard reconstruction. Instead, redundancy is achieved through multiple physical cards that remain in your possession from day one.
Backup is tangible. It lives in the cards users hold, not in a distributed cloud infrastructure operated by separate companies. The security model minimizes external dependencies and keeps control fully in the hands of the wallet owner.
Read more on how Tangem does back ups.
No customer database of seed phrases.
Tangem has no database of seed phrases, no identity-linked key fragments, and no custodial relationship with your cryptographic material. There is nothing for a government to subpoena and nothing for a hacker to target.
Tangem’s business model is hardware sales and commissions from in-app services like Yield Mode, not subscriptions. You buy the cards, hold the cards, and hold your keys. Unlike Ledger, there is no monthly fee to maintain access to your own backup.
Ledger asks you to trust.
Tangem removes the need for trust.