What Are Public and Private Keys in Crypto Wallets? How Do They Work?
Public and private keys are essential to Bitcoin and other cryptocurrencies. They enable you to send and receive cryptocurrency in your wallet without needing a centralized third party to authorize your transactions. These keys are part of the framework for public-key cryptography (PKC) and critical components that ensure the safety of your digital assets. But what exactly are they, and how do they work together to protect your funds?
What is public-key cryptography?
Public-key cryptography (PKC) is a technology that uses asymmetric encryption to validate the authenticity of data. PKC was initially used in traditional computing to encrypt and decrypt messages. This technology is now used by cryptocurrency to encrypt and decrypt transactions.
PKC relies on "trapdoor functions," which are one-way mathematical functions that are simple to solve in one direction but nearly impossible to crack in the opposite. While this is possible, reverse engineering these functions requires a quantum supercomputer and thousands of years.
What is a public key?
A public key is a cryptographic code that enables users to receive cryptocurrency into their accounts. While anyone can send transactions to the public key, the private key is required to "unlock" them and prove that you own the cryptocurrency received in the transaction.
The public key that can receive funds is typically known as an address — a shortened version of your public key. For example, here is the first Bitcoin address ever: 1A1zP1eP5QGefi2DMPTfTL5SLmv7DivfNa.
You can freely share your public key without concern. You may have come across donation pages for content creators or charities that include the public keys to their crypto addresses. While anyone can donate, the private key is required to unlock and access the donated funds.
What is a private key?
A private key is a cryptographic code that allows you to prove ownership and spend funds associated with your public address. This private key can take many different forms:
- A binary code is 256 characters long.
- Hexadecimal code of 64 digits.
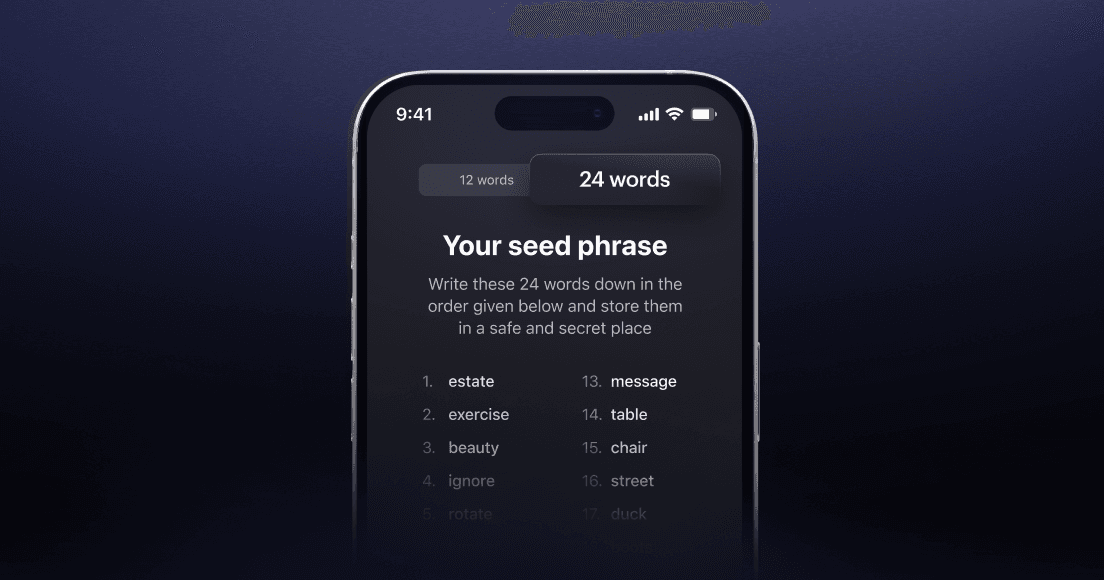
- A QR code.
- Mnemonic seed phrase.
In whatever form it takes, the private key is an astronomically large number — and for good reason. You can use a private key to generate a public key. However, doing the opposite is nearly impossible due to the one-way "trapdoor" function. A private key can also be linked to unlimited public keys.
Warning! Never share your private key with anyone, not even yourself!
How do the private and public keys work?
When you create a wallet, a true random number generator (TRNG) on a secure element generates your private key. It is composed of a long string of alphanumeric characters.
The private key is unique to you and lets you withdraw, transfer, or conduct any other transaction from your wallet.
A complex algorithm uses your private key to generate your public key — a long string of digits compressed and reduced to form the public address.
How does a private key generate public keys in crypto wallets?
A private key generates public keys through asymmetric cryptography, specifically using mathematical algorithms such as Rivest-Shamir-Adleman (RSA), elliptic curve cryptography (ECC), or Digital Signature Algorithm (DSA).
Here's a simplified explanation of how this process works with elliptic curve cryptography, commonly used in many modern blockchains like Bitcoin.
- Choosing an elliptic curve
The first step involves selecting a specific elliptic curve, a mathematical construct with defined properties. In Bitcoin, the widely used curve is called secp256k1.
- Deriving a unique point
The private key is a random number often represented as a large integer. This number is used to derive a unique point on the chosen elliptic curve through a process known as point multiplication.
- Generating the public key
This unique point derived from the private key is the corresponding public key, represented by two coordinates (x, y) on the curve. However, only the x-coordinate is typically used, resulting in a compressed public key.
- Compressing the unique point (Optional)
For efficiency, the full public key can be compressed into a shorter form, which still allows for crypto operations.
- SHA-256 and RIPEMD-160 hashing
In Bitcoin, the compressed public key is hashed twice using the SHA-256 and RIPEMD-160 cryptographic hash functions. This process creates a shorter, fixed-size representation known as the Public Key Hash (PKH), used in Bitcoin addresses.
- Checksum Addition (Optional)
Some blockchain systems add a checksum to the PKH to enhance error detection. This is not always the case in all cryptocurrencies.
- Base58 Encoding
Finally, the PKH (with or without the checksum) is encoded in a format like Base58, eliminating ambiguous characters and making the public address more human-readable.
The resulting address, derived from the public key, is what you see and use when sending or receiving cryptocurrencies.
While it's computationally infeasible to derive the private key from the public key, the reverse process (creating a public key from a private key) is relatively transparent because of the mathematical properties of elliptic curves, allowing users to prove wallet ownership without revealing their private key.
Asymmetric encryption
The two keys work together to encrypt and decrypt messages. When you encrypt a message with a person's public key, the recipient can only decrypt it with the matching private key. As a result, encrypted messages can only be read by the intended recipient. The ability to ensure the sender's identity is another advantage of asymmetric encryption.
For example, you want to send a secret message to your friend, Patrick. You will encrypt the message with Patrick's public key first, then sign it with your private key. Patrick would have to decrypt it with his private key.
How crypto transactions work with private and public keys
Let's use a scenario where you want to send Patrick some Bitcoin. First, You need Patrick's public address, a shorter form of his public key. You then sign the message with your private key to ensure the transaction has not been modified. The transaction is then encrypted and transmitted to be verified by nodes on the Bitcoin network.
Patrick's wallet would then use his private key to decrypt the transaction message and obtain the Bitcoin you sent. Furthermore, Patrick must keep his private key confidential because anyone with access to it will also have access to any associated funds.
Remember that an authentic, mined transaction is irreversible. So verify that you're sending funds to the correct public address on the right network before signing the transaction with your private key.
Where are private keys stored?
Private keys are stored in a cryptocurrency wallet, either mobile or desktop software (hot wallet) or a specialized hardware device (cold wallet).
If you store cryptocurrency on an exchange like Binance or Coinbase, the exchange becomes the custodian of your private keys. In custodial wallets, you're entrusting the custodian with your private keys like you'd entrust a bank's vault with your cash.
In a non-custodial wallet, you have control of your private keys. Fortunately, non-custodial cryptocurrency wallets are configured and function, so you'll rarely have to deal with private keys directly.
The wallets store and sign transactions with them automatically. As a backup, you can have your private keys as a seed phrase or multiple hardware devices to ensure redundancy.
How public and private keys control your cryptocurrency
Understanding how public and private keys interact is critical to understanding crypto transactions. When you say you have cryptocurrency, that statement means that you have a private key proving you own it.
Your philosophy and risk tolerance might influence the decision between "holding your own keys" and trusting a custodian.
If you want total control over your private keys, consider modern hardware wallets like the Tangem Wallet. This waller does an excellent job of managing and never exposing your private keys.
When picking a custodial solution, such as an exchange, choose a reputable company that prioritizes security and regulation.
Conclusion
Think of the public key as your email address and your private key as your password. Anyone can send you an email, but only you can read it by entering your password. Private keys, like email passwords, should be kept to yourself, whereas public keys can be shared.